In our previous article, we discussed Kubernetes Secrets, the mechanisms Kubernetes provides for managing sensitive data. We also highlighted the critical importance of securing secrets in containerized environments. As organizations increasingly adopt Kubernetes for its powerful capabilities in orchestrating containerized applications, understanding and implementing robust security measures for your Kubernetes clusters becomes paramount.
Kubernetes has revolutionized the way we deploy, manage, and scale applications. Its dynamic nature and flexibility have made it an essential tool in the modern DevOps toolkit. However, with great power comes great responsibility. Ensuring the security of your Kubernetes clusters is not just a best practice—it’s a necessity. Securing your cluster protects your applications and data from potential threats and ensures the integrity and availability of your services.
Engineering platforms like Atmosly play a crucial role in this context. By providing automated security checks, centralized monitoring, and resilience strategies, Atmosly enables organizations to secure their Kubernetes clusters efficiently and effectively. This article will explore the best practices and tools for securing your Kubernetes cluster and highlight how platforms like Atmosly can support these efforts.
Understanding Kubernetes Cluster Security
Kubernetes cluster security encompasses a broad set of practices and tools designed to protect a Kubernetes cluster from various threats. It involves securing the cluster's components, including the control plane, nodes, network communications, and the applications running within the cluster. Effective Kubernetes security ensures that only authorized users and services can access the cluster resources, protect sensitive data, and the system is resilient against attacks and failures.
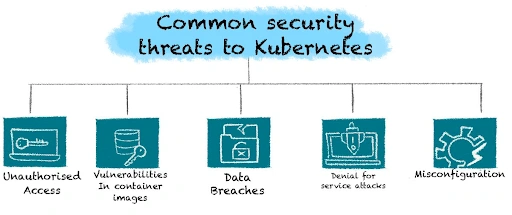
Common Security Threats to Kubernetes Clusters
Kubernetes clusters face a myriad of security threats, including:
- Unauthorized Access: Attackers gaining access to the Kubernetes API server or other critical components can lead to severe security breaches. Ensuring that only authenticated and authorized users can interact with the cluster is vital.
- Vulnerabilities in Container Images: Using vulnerable container images can expose the cluster to security risks. Regularly scanning and updating images is essential to prevent exploitation.
- Data Breaches: Exposing sensitive data through misconfigured secrets or unsecured communications can lead to data breaches. Proper encryption and secure secret management are crucial.
- Denial of Service (DoS) Attacks: Overwhelming the cluster resources through DoS attacks can disrupt services and degrade performance. Implementing rate limiting and resource quotas can mitigate such threats.
- Misconfigurations: Incorrect configurations can create security loopholes, making the cluster susceptible to attacks. Regular audits and compliance checks help identify and rectify misconfigurations.
Client's Responsibilities in Securing Kubernetes Cluster
While Kubernetes provides robust security features, securing a Kubernetes cluster also lies with the clients. Organizations must adopt a proactive approach to security, implementing best practices and leveraging the right tools to protect their clusters. Key responsibilities include:
- Implementing Access Controls: Using Role-Based Access Control (RBAC) to define and enforce permissions, ensuring that users and services have the minimum necessary access.
- Regular Audits and Compliance Checks: Continuously monitoring and auditing the cluster for compliance with security standards and best practices.
- Securing Network Communications: Implementing network policies to control traffic flow and using encryption to protect data in transit.
- Keeping Software Up to Date: Regularly updating Kubernetes components and container images to patch vulnerabilities and enhance security.
- Leveraging Security Tools and Platforms: Utilizing tools like kube-bench, Falco and engineering platforms like Atmosly to automate security checks, monitor for threats, and respond to incidents.
By understanding these aspects of Kubernetes cluster security, organizations can build a robust defense against potential threats and ensure the resilience of their containerized applications.
Why Secure Your Kubernetes Cluster
Securing your Kubernetes cluster is not just an option—it’s necessary to protect sensitive data, ensure compliance, and maintain your applications' overall health and performance. Here's why securing your Kubernetes cluster is critical:
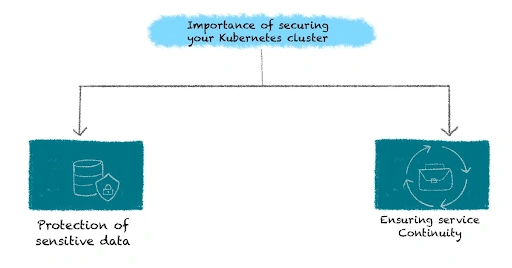
Importance of Securing Your Kubernetes Cluster
- Protection of Sensitive Data:
- Data Integrity and Confidentiality: Kubernetes clusters often handle sensitive information, from user data to proprietary business logic. Securing your cluster ensures that this data is confidential and integral, protecting it from unauthorized access and tampering.
- Compliance with Regulations: Many industries are subject to strict regulations regarding data protection, such as GDPR, HIPAA, and CCPA. Ensuring your Kubernetes cluster is secure helps you comply with these regulations, avoiding legal and financial repercussions.
- Ensuring Service Continuity:
- Preventing Downtime: Security breaches can lead to significant service disruptions. Unauthorized access, data breaches, or attacks such as DDoS can take down services, resulting in downtime and loss of customer trust. Securing your cluster helps prevent these interruptions, ensuring your services remain available and reliable.
- Maintaining Performance: A secure cluster is a well-performing cluster. By preventing unauthorized access and mitigating security threats, you ensure your cluster operates smoothly, providing a consistent and reliable user experience.
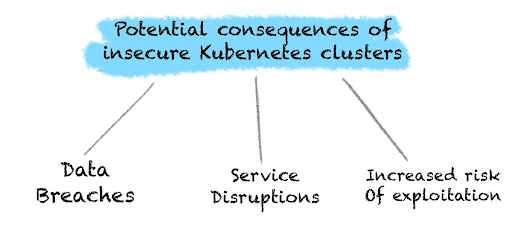
Potential Consequences of Insecure Kubernetes Clusters
- Data Breaches:
- Exposure of Sensitive Information: An insecure Kubernetes cluster can lead to data breaches, exposing sensitive information to malicious actors. This can include personal customer data, financial records, or proprietary business information.
- Financial and Reputational Damage: Data breaches can result in substantial financial losses due to regulatory fines, legal fees, and loss of business. Additionally, they can severely damage your organization’s reputation, eroding customer trust and loyalty.
- Service Disruptions:
- Downtime and Unavailability: Insecure clusters are more vulnerable to attacks that can disrupt services. Downtime not only affects user experience but can also lead to lost revenue and operational inefficiencies.
- Degraded Performance: Security breaches can lead to resource exhaustion, affecting the performance of your applications. This can result in slower response times and a degraded user experience.
- Increased Risk of Exploitation:
- Exploitation of Vulnerabilities: An insecure cluster is an easy target for attackers who can exploit vulnerabilities to gain control over your infrastructure. This can lead to unauthorized access, data theft, and potential sabotage of your services.
- Propagation of Attacks: Once a cluster is compromised, it can serve as a launchpad for further attacks within your infrastructure, affecting other services and systems.
By securing your Kubernetes cluster, you protect your data and ensure compliance while safeguarding your business operations from the detrimental effects of security breaches. Proactive security measures help you maintain control over your infrastructure, ensuring that your applications remain resilient, reliable, and ready to meet your users' demands.
Engineering platforms like Atmosly can play a pivotal role in this process. Atmosly provides robust tools and automated processes to help you secure your Kubernetes clusters efficiently, ensuring that your security practices are comprehensive and practical.
Best Practices for Kubernetes Cluster Security
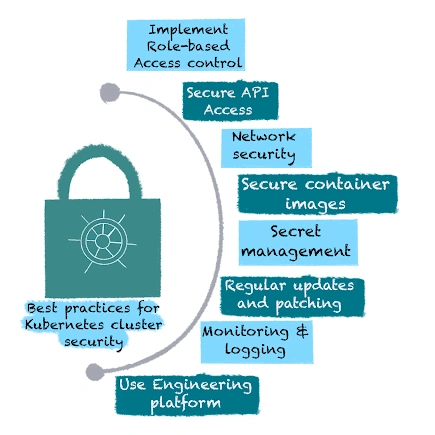
Securing a Kubernetes cluster requires a multifaceted approach that addresses various aspects of the cluster's architecture and operation. Below are some of the best practices for ensuring robust Kubernetes cluster security:
Implement Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a fundamental security mechanism that restricts access to cluster resources based on the roles assigned to users and applications.
- Define Roles and Permissions: Clearly define roles and the associated permissions to ensure that users and services have only the access they need to perform their functions.
- Principle of Least Privilege: Always adhere to the principle of least privilege, granting users and services the minimal necessary permissions.
- Regular Audits: Regularly audit roles and permissions to ensure they align with current needs and security policies.
Secure API Access
The Kubernetes API server is a critical component that manages the cluster. Ensuring its security is paramount.
- Use Strong Authentication Methods: Implement robust authentication methods, such as OAuth2, to verify the identities of users and services accessing the API server.
- Encrypt API Traffic: Use TLS to encrypt traffic between the API server and clients to protect data in transit from eavesdropping and tampering.
- Restrict Access: Limit API access to trusted networks and use network policies to control traffic to the API server.
Network Security
Securing the network communications within a Kubernetes cluster is essential to prevent unauthorized access and data breaches.
- Network Policies: Use Kubernetes network policies to control traffic flow between pods, ensuring that only authorized communication paths are allowed.
- Segmentation: Implement network segmentation to isolate different parts of the cluster, reducing the blast radius of potential security incidents.
- Encrypt Data in Transit: Encrypt all sensitive data transmitted over the network to protect it from interception.
Secure Container Images
Container images are the building blocks of Kubernetes applications. Ensuring their security is crucial to prevent vulnerabilities from being introduced into the cluster.
- Use Trusted Sources: Only use container images from trusted sources and verify their integrity before deployment.
- Regular Scanning: Regularly scan container images for vulnerabilities using tools like Clair or Trivy and promptly address any identified issues.
- Minimal Base Images: Use minimal base images to reduce the attack surface and include only the necessary dependencies.
Secret Management
Properly managing sensitive data such as passwords, tokens, and keys is critical for maintaining cluster security.
- Use Kubernetes Secrets: Store sensitive information using Kubernetes Secrets designed explicitly for managing confidential data.
- Encrypt Secrets: Encrypt secrets at rest and use encryption keys managed by a secure key management service (KMS).
- Access Control: Implement strict access controls to ensure only authorized pods and users can access the secrets.
Regular Updates and Patching
Keeping Kubernetes components and dependencies up to date is essential for maintaining security.
- Patch Management: Regularly apply security patches and updates to the Kubernetes components, operating system, and other dependencies.
- Version Management: Keep track of Kubernetes version releases and plan for regular upgrades to benefit from the latest security enhancements and bug fixes.
Monitoring and Logging
Effective monitoring and logging are crucial for detecting and responding to security incidents.
- Centralized Logging: Implement centralized logging to collect and analyze logs from all cluster components and applications.
- Monitor Metrics: Use monitoring tools to track key metrics and set up alerts for suspicious activities or performance anomalies.
- Incident Response: Develop and maintain an incident response plan to quickly address and mitigate security incidents.
Use Engineering Platforms
Engineering platforms like Atmosly provide essential tools and automation capabilities to enhance Kubernetes cluster security.
- Automated Security Checks: Leverage Atmosly to automate regular security checks and compliance audits.
- Centralized Management: Use Atmosly to manage security policies, access controls, and monitoring.
- Resilience Strategies: Implement resilience strategies using Atmosly’s tools to ensure that your cluster can withstand and recover from security incidents.
By following these best practices, organizations can significantly enhance the security of their Kubernetes clusters, ensuring that their applications and data are protected against a wide range of threats.
Tools for Securing Your Kubernetes Cluster
Securing a Kubernetes cluster involves using specialized tools designed to identify vulnerabilities, enforce security policies, and monitor for suspicious activities. Here are some of the key tools you can use to enhance the security of your Kubernetes clusters, along with an explanation of their benefits and how they can be integrated with engineering platforms like Atmosly for centralized security management.
Kube-bench
Kube-bench is a tool that checks whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes Benchmark. It helps ensure that your cluster configurations adhere to industry best practices.
- Security Audits: Kube-bench performs a thorough audit of your Kubernetes cluster against the CIS benchmarks, highlighting areas that need attention.
- Compliance Checks: It ensures your cluster meets compliance requirements, providing detailed reports that can guide your security improvements.
- Regular Scans: Integrate kube-bench into your CI/CD pipeline to run regular scans, ensuring continuous compliance and security.
Here's how you can get started with Kube-bench to secure your Kubernetes cluster:
Kube-bench:
# Run kube-bench for a specific Kubernetes version
kube-bench --version <kubernetes_version>Kube-hunter
Kube-hunter is a tool designed to perform penetration tests on Kubernetes clusters, identifying potential vulnerabilities and security weaknesses.
- Threat Detection: Kube-hunter simulates attacks on your Kubernetes cluster to identify vulnerabilities that could be exploited by malicious actors.
- Detailed Reports: It provides detailed reports of the findings, including each vulnerability's severity and potential impact.
- Proactive Security: By regularly running Kube-hunter, you can proactively identify and address security gaps before they are exploited in real-world scenarios.
Here's how you can get started with Kube-hunter to secure your Kubernetes cluster:
Kube-hunter:
# Perform an active scan on your cluster
kube-hunter --remote <cluster_ip>Falco
Falco is a runtime security tool that monitors the behavior of your Kubernetes cluster and detects anomalies, providing real-time alerts for suspicious activities.
- Behavioral Monitoring: Falco continuously monitors the behavior of containers and applications, detecting deviations from expected behavior.
- Real-time Alerts: It generates real-time alerts for security events, enabling prompt response to potential incidents.
- Policy Enforcement: Falco allows you to define custom security policies to enforce specific security standards within your cluster.
Here's how you can get started with Falco to secure your Kubernetes cluster:
Falco:
# Install Falco in your cluster
helm install falco stable/falco
# Define a custom rule for Falco
rule: Write below /etc
desc: An attempt to write to /etc
condition: fd.name startswith /etc and evt.is_write
output: "File write detected below /etc: %evt.arg.res"
priority: ERRORIntegrating Kubernetes Cluster Security Tools With Atmosly
Engineering platforms like Atmosly can significantly enhance the effectiveness of these security tools. It can provide centralized management and automation capabilities as follows.
- Automated Workflows: Atmosly automates security workflows, such as running regular scans with kube-bench and kube-hunter. This ensures continuous security without manual intervention.
- Implementing Guardrails: Atmosly support implementation of Open Policy agent which helps in putting correct guardrails in place to keep the Kubernetes cluster secure and as per the requirements of the organization security standards
- Implementation of DevSecOps: Tools like Trivy can be deployed at the cluster level and at pipeline level which scan the container images for any vulnerabilities during the pipelines and also across the cluster for continuous scanning
- Enhanced Collaboration: Atmosly facilitates collaboration among DevOps, security teams, and other stakeholders by providing a shared platform for managing security incidents and implementing remediation strategies.
How to Secure Your Kubernetes Cluster
Securing a Kubernetes cluster involves a comprehensive approach that includes configuring access controls, network policies, and security tools. Below is a step-by-step guide to securing your Kubernetes cluster effectively:
Step 1: Set Up Role-Based Access Control (RBAC)
RBAC is essential for controlling who can access and perform actions within your cluster.
- Create Roles: Define roles with specific permissions that align with the principle of least privilege.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: default
name: read-pods
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "watch", "list"]
- Create Role Bindings: Bind the roles to users or service accounts.
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: read-pods-binding
namespace: default
subjects:
- kind: User
name: "jane-doe"
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: read-pods
apiGroup: rbac.authorization.k8s.io
Step 2: Implement Network Policies
Network policies control traffic flow at the IP address level, providing an essential layer of security.
- Define Network Policies: Specify the allowed traffic between pods.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-same-namespace
namespace: default
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
ingress:
- from:
- podSelector: {}
egress:
- to:
- podSelector: {}
- Apply Network Policies: Use kubectl apply to implement the policies.
kubectl apply -f network-policy.yaml- Monitor Traffic: Use tools like Calico or Weave to manage and monitor network policy.
Step 3: Configure Security Tools
Using specialized security tools helps in continuously monitoring and improving your cluster's security posture. We will be using Kube-bench and Falco here, as shown below;
- Install Kube-bench: Check cluster compliance against CIS benchmarks.
kubectl apply -f https://github.com/aquasecurity/kube-bench/blob/main/job.yaml- Run Kube-hunter: Perform penetration testing to identify vulnerabilities.
docker run -it --rm --name kube-hunter aquasec/kube-hunter --remote <cluster_ip>- Deploy Falco: Monitor runtime security and detect anomalies.
helm install falco falcosecurity/falco- Automate with Atmosly: Use Atmosly to automate these tools and integrate their outputs for a comprehensive security overview to achieve the following;
- Automated Scans: Schedule regular kube-bench scans.
- Penetration Testing: Automate kube-hunter tests within CI/CD pipelines.
- Real-time Monitoring: Set up Falco alerts and integrate with Atmosly for centralized incident management.
Step 4: Secure API Access
Protecting the Kubernetes API server is critical for maintaining control over the cluster.
- Enable Authentication: Use secure authentication mechanisms.
--token-auth-file=/path/to/token/auth/file- Use TLS: Encrypt API server traffic.
--tls-cert-file=/path/to/cert/file
--tls-private-key-file=/path/to/key/file- Restrict Access: Limit API access to trusted networks using firewall rules and network policies.
Step 5: Manage Secrets Securely
Handling sensitive information securely is crucial for protecting your cluster.
- Store Secrets in Kubernetes: Use Kubernetes Secrets to manage sensitive data.
apiVersion: v1
kind: Secret
metadata:
name: my-secret
namespace: default
type: Opaque
data:
username: <base64-encoded-username>
password: <base64-encoded-password>
- Encrypt Secrets: Enable encryption at rest for secrets.
--experimental-encryption-provider-config=/path/to/encryption/config.yaml- Access Control: Ensure only authorized pods and users can access secrets.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: default
name: secret-reader
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get"]
Following this step-by-step guide, you can implement robust security measures that protect your Kubernetes cluster from a wide range of threats. These practices and integrating advanced security tools and platforms like Atmosly will help you maintain a secure, resilient, and compliant Kubernetes environment.
Conclusion
In this article, we have delved deeply into securing Kubernetes clusters, a foundational element of modern containerized applications. Understanding the importance of Kubernetes security is paramount as it directly influences protecting sensitive data, compliance with regulatory requirements, and your applications' overall stability and reliability.
We introduced Kubernetes and its significance in today's technology landscape, emphasizing the need for robust security measures to safeguard these clusters. We discussed the fundamental principles of Kubernetes cluster security, including identifying common threats such as unauthorized access, vulnerabilities, and data breaches. Securing a Kubernetes cluster is a shared responsibility, requiring diligent efforts from both service providers and clients.
Highlighting why securing your Kubernetes cluster is essential, we underscored the potential consequences of neglecting security, such as data breaches and service disruptions. The benefits of a secure Kubernetes environment include enhanced data protection, compliance with industry standards, and the assurance of uninterrupted service delivery.
We provided a comprehensive list of best practices for securing your Kubernetes cluster. These practices encompass:
- Role-Based Access Control (RBAC): Implementing fine-grained access control to limit user permissions.
- Network Policies: Defining rules for pod communication to prevent unauthorized access.
- Pod Security Policies (PSP): Enforcing security standards at the pod level to minimize vulnerabilities.
- Image Scanning: Regularly scanning container images for vulnerabilities to ensure only secure images are deployed.
- Secret Management: Securely managing sensitive information and credentials.
Additionally, we explored several powerful tools designed to bolster Kubernetes security:
- kube-bench: This is used to audit Kubernetes clusters against security benchmarks.
- kube-hunter: This is used to identify vulnerabilities within the cluster.
- Falco: For real-time security monitoring and intrusion detection.
Integrating these tools with an engineering platform like Atmosly enables centralized security management, automating best practices and enhancing overall security posture.
The step-by-step guide on securing your Kubernetes cluster provided practical instructions, covering the setup of RBAC, implementation of network policies, and configuration of essential security tools. We also discussed handling common security threats, such as container escapes and pod security issues, offering mitigation strategies and best practices for incident response.
Finally, we highlighted the pivotal role of engineering platforms like Atmosly. Atmosly simplifies and automates the complex processes involved in Kubernetes security management. By providing a unified dashboard, automated alerts, policy enforcement, and continuous monitoring, Atmosly ensures that your Kubernetes clusters are not only secure but also resilient against emerging threats.
In conclusion, securing your Kubernetes cluster is not a one-time effort but an ongoing process. It requires a proactive approach, leveraging best practices, robust tools, and comprehensive platforms like Atmosly. By doing so, you can protect sensitive data, maintain compliance, and ensure the reliability and security of your modern applications. Embracing these strategies will empower your organization to confidently navigate the complexities of Kubernetes security, fortifying your clusters against potential threats and ensuring smooth, uninterrupted operations.






