Introduction
Modern engineering teams ship faster than ever — but only when their pipelines keep up.
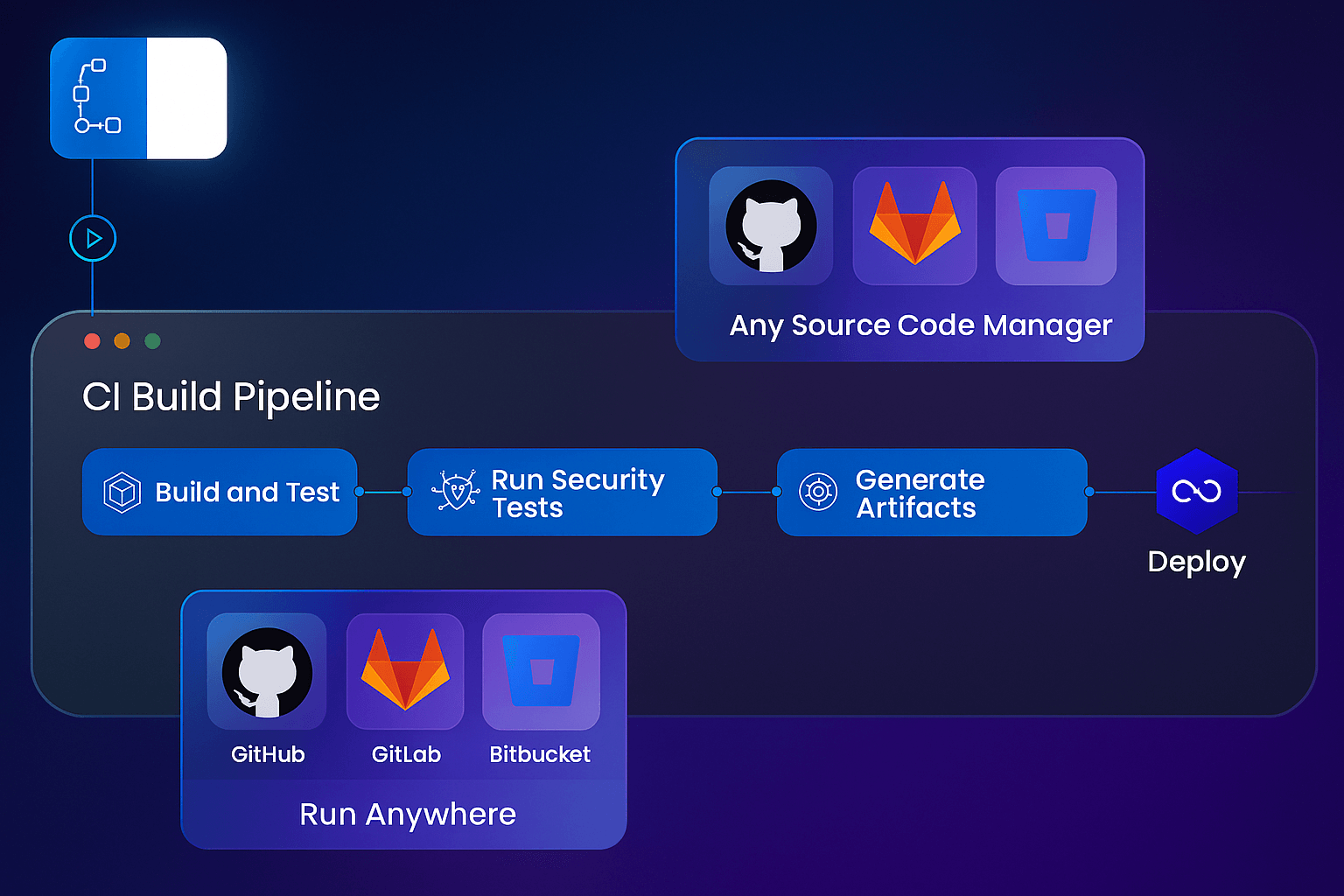
A well-designed CI/CD pipeline automates everything from code commit to production deployment, catching issues early and keeping releases safe.
If you’ve been manually running builds or copying deployment scripts, it’s time to rethink your workflow. In this guide, we’ll unpack what a CI/CD pipeline is, how the stages fit together, best practices for reliability, and what changes when you deploy to Kubernetes.
You’ll also see how you can create and manage pipelines visually using Atmosly’s Pipeline Builder — no YAML required.
[Image: hero banner showing ci cd flow]
What Is a CI/CD Pipeline and Why It Matters
CI/CD stands for Continuous Integration and Continuous Delivery / Deployment.
Continuous Integration ensures that every code change is automatically built and tested. Continuous Delivery and Deployment automate the rest — packaging, approvals, rollout, and monitoring.
When done right, this workflow gives you:
• Faster releases without manual hand-offs
• Higher quality through consistent testing
• Predictable deployments — no “works on my machine” moments
• Confidence to ship multiple times a day
In short: automation turns deployment from an event into a habit
CI/CD Pipeline Stages
Although pipelines vary across stacks, most follow six essential stages.
Source / Trigger
Everything starts with a code push, merge request, or scheduled run. The pipeline watches for changes and triggers automatically — no manual kickoff needed.
Build / Package
Code is compiled or containerized. The goal is to produce a consistent artifact once, then promote that same artifact across environments.
Test / Validate
Automated unit, integration, and smoke tests verify correctness. Fast feedback here saves hours later.
Scan / Security Gates
Before promoting code, scan dependencies for vulnerabilities, secrets, and license issues.
This is where Atmosly’s Pipeline Builder shines — it includes Trivy and Detect-Secrets scanners out of the box.
Deploy / Release
The pipeline ships your artifact to staging or production using deployment strategies like rolling, blue-green, or canary.
Monitor / Rollback
Post-deployment monitoring checks health metrics and triggers automatic rollback if thresholds fail.
Kubernetes CI/CD Deployment Strategies (Rolling, Canary, Blue-Green)
Kubernetes brings powerful deployment primitives. Here are the most common patterns and when to use them:
• Rolling Update – Default strategy; replaces pods gradually with minimal downtime.
• Blue/Green Deployment – Keep two environments; deploy to “green,” test, then switch traffic from “blue.” Easy rollback.
• Canary Release – Send a small percentage of traffic to the new version, monitor, then ramp up safely.
• Recreate – Stop old pods, start new ones. Simple but causes downtime.
• Progressive Delivery / Feature Flags – Control exposure through toggles or percentage rollout.
Inside Atmosly’s Pipeline Builder, you can visually choose these strategies — no Kubernetes manifests required — and trigger instant rollback if metrics degrade.
CI/CD vs GitOps — Understanding the Difference
CI/CD and GitOps are often mentioned together, but they represent two complementary philosophies in software delivery.
CI/CD automates the path from code to deployment. Developers push code, and a pipeline builds, tests, scans, and deploys it automatically. The focus is on speed and repeatability.
GitOps, on the other hand, focuses on state management. The desired state of your infrastructure and applications lives in a Git repository. Any change is made via a pull request and automatically reconciled in the cluster.
Think of CI/CD as the vehicle that delivers your changes, while GitOps ensures what’s deployed matches what’s declared.
Many modern teams combine both approaches — using CI/CD pipelines for building, testing, and validating, and GitOps (via tools like ArgoCD or Flux) for continuous reconciliation.
Atmosly’s visual pipeline builder works equally well with GitOps, letting you choose whether to deploy directly or commit manifest updates for a GitOps agent to apply.
CI/CD Best Practices for 2025 and Beyond
Commit Small, Commit Often
Frequent, atomic commits mean faster feedback and fewer merge conflicts.
Build Once, Promote Everywhere
Build your artifact a single time, then deploy the same binary across staging and production to eliminate drift.
Automate Everything
Manual steps introduce inconsistency. From testing to promotion to rollback — script it or use a platform that does.
Shift Security Left
Bake in scans for vulnerabilities, secrets, and compliance. Atmosly integrates scanners directly into pipeline stages so developers fix issues before release.
Parallelize and Cache
Speed up builds by running tasks in parallel and caching Docker layers or dependencies. Explore caching patterns
Monitor DORA Metrics
Track deployment frequency, change failure rate, and mean time to restore. Use pipeline analytics to measure improvement over time.
Use Policy Gates and Approvals Smartly
Approvals aren’t the enemy of velocity — they’re a safety net. Automate rules (for example, auto-approve low-risk changes) to balance governance and speed.
Standardize Pipelines
Provide templates so each team builds on a known baseline. Atmosly lets organizations define reusable pipeline blueprints shared across projects.
Keep Environments Ephemeral
Spin up test environments on demand and tear them down automatically. It keeps clusters clean and costs predictable. Explore environment cloning
Make It Visible
Dashboards, notifications, and logs keep everyone aligned. Atmosly’s built-in pipeline dashboard surfaces history, duration, and outcomes in one view.
Choosing the Right CI/CD Tool
The DevOps landscape offers dozens of CI/CD tools, and selecting the right one depends on your scale, security, and workflow preferences.
Jenkins
- The original CI/CD powerhouse.
- Great flexibility and plugin support, but maintenance-heavy.
- Best for teams with deep DevOps expertise and self-hosting capacity.
GitHub Actions
- Built directly into GitHub repositories.
- Ideal for teams that live in GitHub and want lightweight automation.
- Limitations appear with complex, multi-environment deployments.
GitLab CI/CD
- Unified platform combining SCM, issues, and pipelines.
- YAML-driven, great visibility, but less suited for hybrid or multi-cloud setups.
Tekton / Argo Workflows
- Kubernetes-native, designed for container workloads.
- Highly extensible, but often requires steep learning curve.
Atmosly Pipeline Builder
- Visual, no-YAML approach.
- Native support for DevSecOps stages, policy approvals, and Kubernetes deployment strategies.
- Multi-cloud by design — deploy to AWS, GCP, or Azure clusters seamlessly.
If you’re moving fast and want developer self-service without maintaining Jenkins nodes or managing YAML sprawl, a visual pipeline tool like Atmosly bridges the gap between flexibility and simplicity.
Comparing Top Continuous Integration Tools for CI/CD Pipelines in 2025
| Tool | Best For | Deployment Type | Kubernetes Support | Pipeline Approach | Key Strengths | Limitations | Ideal Use Case |
|---|---|---|---|---|---|---|---|
| Atmosly | Teams needing visual, self-service CI/CD for Kubernetes | SaaS (cloud-hosted) | ✅ Native (multi-cluster agent) | Visual builder with YAML export | - Built-in caching, GitOps sync, OPA & cost insights - One-click deploys with Argo & Helm - Policy enforcement for DevSecOps | - Focused on Kubernetes; not general purpose | SaaS teams deploying microservices or containerized workloads across clusters |
| Jenkins | Enterprises with existing legacy CI setups | Self-hosted / VM-based | ⚙️ Supported via plugins | Declarative pipelines (Jenkinsfile) | - Mature ecosystem, huge plugin library - Extensible for any language or toolchain | - High maintenance overhead - Weak UI/UX, slower scaling | Traditional enterprises with large on-prem infrastructure |
| GitHub Actions | Developer-first, GitHub-native projects | Cloud (GitHub-hosted runners) | ⚙️ Integrates via Actions & Kubernetes secrets | YAML-based workflows | - Tight GitHub integration - Quick setup for repo events - Growing marketplace of actions | - Limited customization for long-running jobs - Cost scales fast for large orgs | Startups or OSS projects already on GitHub |
| GitLab CI/CD | End-to-end DevOps platform users | Cloud / Self-managed | ✅ Good native integration | YAML config in .gitlab-ci.yml | - Unified SCM + CI/CD - Strong RBAC & security scanning - Auto DevOps templates | - Heavier setup for large teams - Limited visibility across clusters | Enterprises consolidating DevSecOps in one platform |
| CircleCI | Fast-moving teams needing cloud CI/CD | Cloud / Hybrid | ⚙️ Via orbs & API integrations | Config-as-code YAML | - Great parallelization - Fast builds, excellent UI - Managed runners | - Limited deep Kubernetes integrations | Teams prioritizing build speed and scalability |
| Tekton Pipelines | Kubernetes-native, open-source adopters | Self-managed on K8s | ✅ Fully native | YAML CRDs (Tasks, Pipelines) | - Cloud-agnostic, open-source CNCF project - Fine-grained control, reusable Tasks | - Requires cluster maintenance - No UI (needs dashboard integration) | Platform teams building internal CI/CD frameworks |
| Argo Workflows | Complex, DAG-based workflows in K8s | Self-hosted on Kubernetes | ✅ Native | YAML DAG definitions | - Excellent for multi-step automation - Deep Kubernetes integration - Argo CD synergy | - Not beginner-friendly - Requires observability add-ons | Teams automating container build/deploy/test pipelines |
| Azure DevOps Pipelines | Microsoft ecosystem users | Cloud / Hybrid | ⚙️ Supported via agents | YAML / Classic editor | - Seamless with Azure Repos & Boards - Enterprise governance controls | - Azure-centric focus | Enterprises using Azure services & AD authentication |
| AWS CodePipeline | AWS-centric applications | Fully managed | ⚙️ Supported via EKS/CodeBuild | GUI & JSON configs | - Tight AWS integration - Pay-per-use pricing | - AWS-only - Limited multi-cloud visibility | Organizations fully on AWS stack |
| Google Cloud Build | GCP workloads / Cloud Run / GKE users | Fully managed | ✅ Native to GKE | YAML steps | - Fast builds with strong GKE integration - Serverless scale | - GCP-specific - Limited external integrations | Startups or ML teams in GCP ecosystem |
Each CI/CD tool serves unique needs for scalability, integration, and Kubernetes support.
Atmosly stands out as a Kubernetes-native SaaS uniting CI/CD automation, cost insights, and security.
Jenkins remains powerful yet maintenance-heavy, while GitHub Actions, GitLab, and CircleCI focus on speed and simplicity.
Open-source options like Tekton and Argo offer maximum flexibility for platform teams building secure, reliable DevSecOps pipelines.
Designing Secure and Reliable Pipelines (DevSecOps)
Security can’t be an afterthought. A secure pipeline covers three areas:
• Code security – static analysis, dependency checks, secrets detection.
• Infrastructure security – scanning container images and manifests.
• Process security – approvals, audit logs, and role-based access.
In Atmosly’s Pipeline Builder, these checks are part of the workflow — not add-ons. You can fail a build automatically if a high-severity vulnerability appears or require re-approval after remediation.
Example: A Kubernetes CI/CD Pipeline in Action
Let’s visualize a real example for a Node.js service deploying to Kubernetes.
- Trigger: Push to the main branch
- Build: npm install, lint, unit tests, Docker build, push to registry
- Scan: Trivy vulnerability scan, Detect-Secrets, Sonar analysis
- Deploy to Staging: Rolling update + smoke tests
- Approval Gate: Notify reviewer; auto-approve if tests & scans pass
- Deploy to Production: Canary release, shift 25% → 100% after 30-minute success
- Monitor & Rollback: Health checks fail → instant rollback to previous revision
The same flow in Atmosly takes minutes — drag “Source,” “Build,” “Scan,” “Deploy,” and “Monitor” nodes, link them visually, and save.
No YAML files, no indentation errors — just outcomes.
Common Pitfalls to Avoid
• Over-engineering the first pipeline — start simple and iterate.
• Mixing build and deploy environments — keep them separate to prevent leaks.
• Skipping rollback testing — always verify rollback paths.
• No visibility into metrics — track duration, failure rate, and MTTR.
• Hard-coding secrets — use a secrets manager integrated into the pipeline.
• Ignoring cost efficiency — parallel jobs are great until cloud bills rise. Atmosly helps visualize and control resource usage.
Common Metrics to Track in CI/CD
To continuously improve, teams should measure how effectively their pipeline delivers value.
The DORA metrics are the gold standard for DevOps performance:
- Deployment Frequency: How often you deploy code to production.
- Lead Time for Changes: How long it takes from code commit to release.
- Mean Time to Restore (MTTR): How fast you recover from incidents.
- Change Failure Rate: The percentage of deployments that cause production issues.
Healthy engineering teams deploy frequently, recover quickly, and have a low failure rate.
Atmosly provides built-in analytics dashboards that visualize these metrics automatically across all your projects, giving engineering leaders a real-time health score for delivery performance.
Future of CI/CD — Where It’s Headed
CI/CD is evolving beyond pipelines that just automate builds and tests.
Over the next few years, several shifts are redefining how teams approach delivery.
1. AI-Assisted Pipelines
AI is helping developers write, debug, and optimize pipelines. Expect tools that suggest build optimizations, auto-detect flaky tests, or recommend parallelization opportunities.
2. Continuous Verification
It’s no longer enough to deploy; teams want automated post-deployment checks — verifying business KPIs, error rates, and user impact before fully rolling out.
3. Policy-Driven Automation
Security and compliance teams are introducing guardrails directly in pipelines. With built-in policy engines like OPA, Atmosly already allows conditional approvals, ensuring compliance without slowing engineers down.
4. Unified Observability
Future pipelines will integrate logs, metrics, and traces at every stage, so teams can debug issues without switching tools.
5. Developer Self-Service Platforms
Platform engineering is reshaping CI/CD. Instead of every team building its own pipelines, companies are adopting self-service platforms where developers pick a blueprint — like “Node.js microservice” — and the rest happens automatically.
This is exactly where Atmosly positions itself: a platform engineering layer that democratizes DevOps through automation and visual workflows.